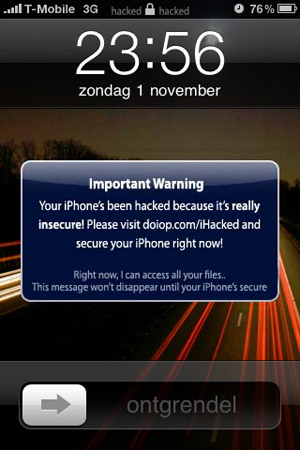
Though jailbreaking an iPhone certainly opens up opportunities to add functionality that Apple doesn't approve of, it can also make an iPhone less secure. Several Dutch iPhone users found that out the hard way after a hacker attacked a number of vulnerable phones on T-mobile Netherlands and tried to extort �5 from them.
It appears one enterprising Dutch hacker used port scanning to identify jailbroken iPhones on T-mobile Netherlands with SSH running. Enabling SSH is a common procedure for jailbroken iPhones, allowing a user to log in via Terminal and run standard UNIX commands. Unfortunately, iPhones all have a default root password that many forget to change after jailbreaking, leaving their phone as vulnerable as a Lamborghini parked on a public street with the windows down, the doors unlocked, and the keys in the ignition.
The hacker relied on unchanged root passwords to hack into the phones. He then sent what appears to be an SMS alert to the hacked phones (in reality it's a replaced wallpaper) that read, "You iPhone's been hacked because it's really insecure! Please visit doiop.com/iHacked and secure your iPhone right now! Right now, I can access all your files." Going to the website directs the user to send �5 to a PayPal account, after which the hacker will e-mail instructions to remove the hack—which most likely involve restoring the iPhone to factory settings.
The hacker doesn't appear to have malicious intent, other than to glean some extra cash. "If you don't pay, it's fine by me," reads the page mentioned in the message to the hacked iPhone owners. "But remember, the way I got access to your iPhone can be used by thousands of others—they can send text messages from your number (like I did), use it to call or record your calls, and actually whatever they want, even use it for their hacking activities! I can assure you, I have no intention of harming you or whatever, but, some hackers do! It's just my advice to secure your phone."
An Ars reader familiar with computer security let us know that security researchers have done similar port scanning in the past, and downloaded users' SMS databases as a "proof of concept." However, this is the first time that it seems the technique has been used in the wild. It's worth noting that the technique is fairly trivial and could be done by anyone with even a modicum of networking know-how.
The incident highlights the fact that jailbreaking removes the security mechanisms that Apple has in place for the iPhone OS—which are as much about securing the device against hackers as they are about preventing "unauthorized" applications. If you do jailbreak, then the onus of security is on you, so be sure to change the root password to something other than the default. You can also disable the SSH daemon when not in use to prevent this particular attack from happening to you.
UPDATE: It appears the young hacker has had a change of heart on the money issue, and posted instructions for undoing what he did to several Dutch iPhone users. According to a commenter below, he has also apologized for asking for money and returned whatever ill-gotten gains he received from his stunt. However, that doesn't mean someone else couldn't pull the same trick and just not tell you about it. So for goodness sake, if you jailbreak and do things like leave an SSH daemon running, change the default passwords.
reader comments
48